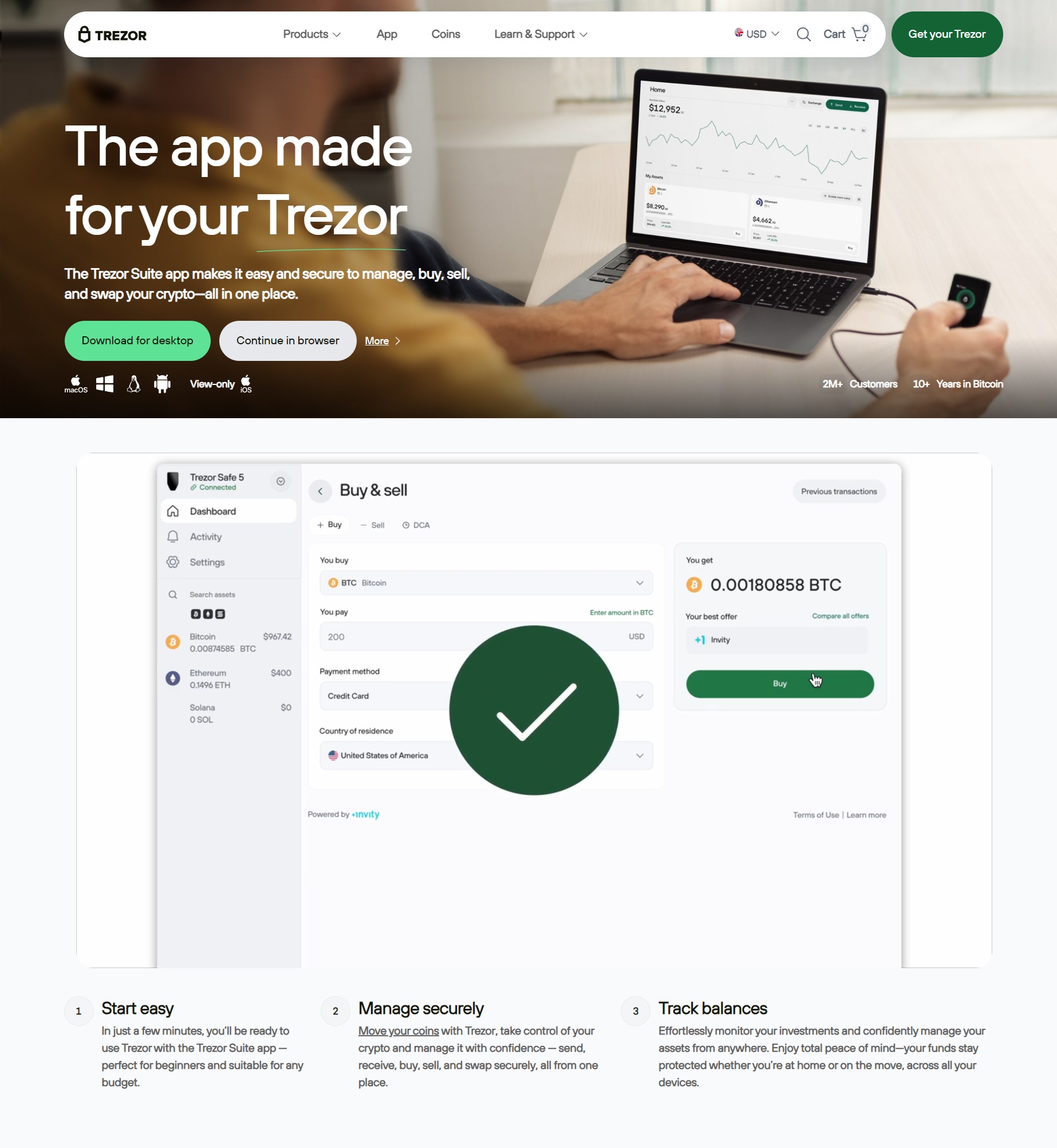
Introduction
Trezor Bridge is the small but essential connectivity layer that links your Trezor hardware wallet to desktop and browser-based applications. Acting as a trusted messenger, the Bridge handles encrypted requests and responses between an application and the device so that your private keys remain isolated and never touch the internet-connected software.
This presentation explains why this separation matters, highlights the new user-facing improvements introduced with the latest app, and provides step-by-step guidance and best practices to keep your crypto holdings secure.
Core Principles
Security First
The Bridge ensures all communications are signed and validated locally. Only minimal, necessary commands are passed through, and any request that requires signing is confirmed on the hardware device itself — ensuring keys never leave secure hardware.
Reliable Connectivity
Designed to be lightweight and cross-platform, Trezor Bridge runs on major operating systems and mediates between browsers, native apps, and the hardware. It reduces compatibility headaches and provides a consistent connection model for developers and end users.
User-Centered Design
Paired with a refreshed Trezor app experience, the Bridge supports clearer transaction summaries, contextual prompts, and a curated dApp discovery area. The focus is on clarity: what you’re signing and why, before the hardware confirmation step.
Getting Started — Quick Setup
To begin, download the official Trezor Bridge installer for your operating system from the verified Trezor site, then install the companion application. After initial setup, connect your hardware wallet via USB (or supported transport) and follow the on-screen pairing flow. Confirming actions on-device completes secure operations — simple and transparent.
- Download Bridge from the official Trezor domain and run the installer.
- Install the Trezor companion app and open it.
- Plug in your device and follow pairing prompts.
- Always verify transaction details on the hardware screen before confirming.
Best Practices
To protect your assets, follow a few essential rules: always download software only from official sources and verify signatures where available; keep both device firmware and Bridge/app software up to date; store your recovery seed offline in multiple secure locations; and avoid using unfamiliar or public networks for critical operations.
Practical Benefits & Use Cases
Everyday users benefit from clear signing flows and reduced risk of accidental approvals. Developers and power users appreciate the stable transport abstraction the Bridge provides, enabling apps to focus on UX rather than low-level connectivity. Institutions gain predictable signing workflows for audits and multi-user approvals.
Conclusion
Trezor Bridge is more than a connector — it is the secure gateway that preserves the core promise of hardware wallets: your keys remain offline and in your control. When combined with a thoughtfully designed app and sensible security practices, the Bridge delivers a robust, user-friendly path into Web3.